Want to listen instead?
We want to raise general awareness around a recent Microsoft SharePoint Phishing Scam that has been on the rise recently. What makes this scam so concerning is just how difficult it is to catch unless you know what to look for.
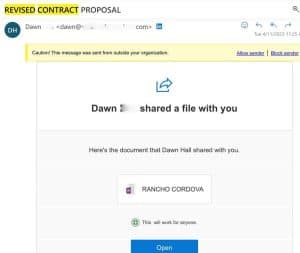
The attack starts via a specially crafted email. The email message appears to be a legitimate file share from a legitimate source (often coming from a compromised partner’s account to lend credibility). Here is a screenshot of the exact email we encountered, but there are many variations:
Although the link takes the user to a different domain than the originating sender, clicking the link takes you to a legitimate SharePoint site:
The attempt to harvest credentials (steal passwords and 6-digit multi-factor authentication codes) takes place when an unsuspecting user clicks the “View document” link shown above (or something similar in other cases).
The potential victim is then taken to what appears to be a legitimate O365 login page, which prompts for credentials. As the link originated from a legitimate SharePoint site, email security filtering technology trusts it, and it seems to the user to be a valid prompt for their credentials. Furthermore, the original email often comes from a trusted partner whose account has been compromised, which makes it even more difficult to detect.
Unfortunately, the redirected site is, in fact, a method of credential harvesting by attackers. When the victim enters their credentials, including MFA code, the attackers then immediately use that information to log in to the victim’s own 365 tenant gaining access.
In order to protect against this type of attack, we recommend the following:
- Be wary of unexpected shared SharePoint files/folders. Consider contacting the sender to confirm they shared the SharePoint link with you.
- Be diligent in inspecting website addresses before entering any credentials or accepting a downloaded file.
- Consider branding your organization’s O365 sign-in page and letting users know not to enter credentials on non-branded pages.
- Consider using push authentication with number matching through the Authenticator app for multi-factor authentication (MFA) (disallow 6 digit codes via text or app). This alone would mitigate this attack.
- We block sign ins from non-Azure AD-Joined Windows machines which significantly helps mitigate the risk.
- Consider blocking non-US top-level domains with Sophos Web Control (recent examples have resulted in pages hosted at URLs ending in .ru (Russia), for example).
- Please share this attack scenario with your employees for awareness.
Stay Secure!